1.8 KiB
Ethical Hacking Assignment 3 - Aidan Sharpe
Task 1 - Network Configuration Between Kali and Metasploitable
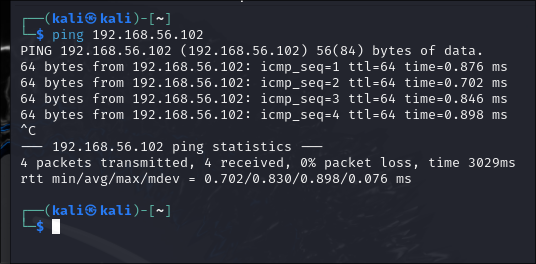
Ensure proper network connectivity between the attacker (Kali Linux) and victim (Metasploitable) virtual machines.
- Configure both Kali Linux and Metasploitable VMs to use host-only adapters
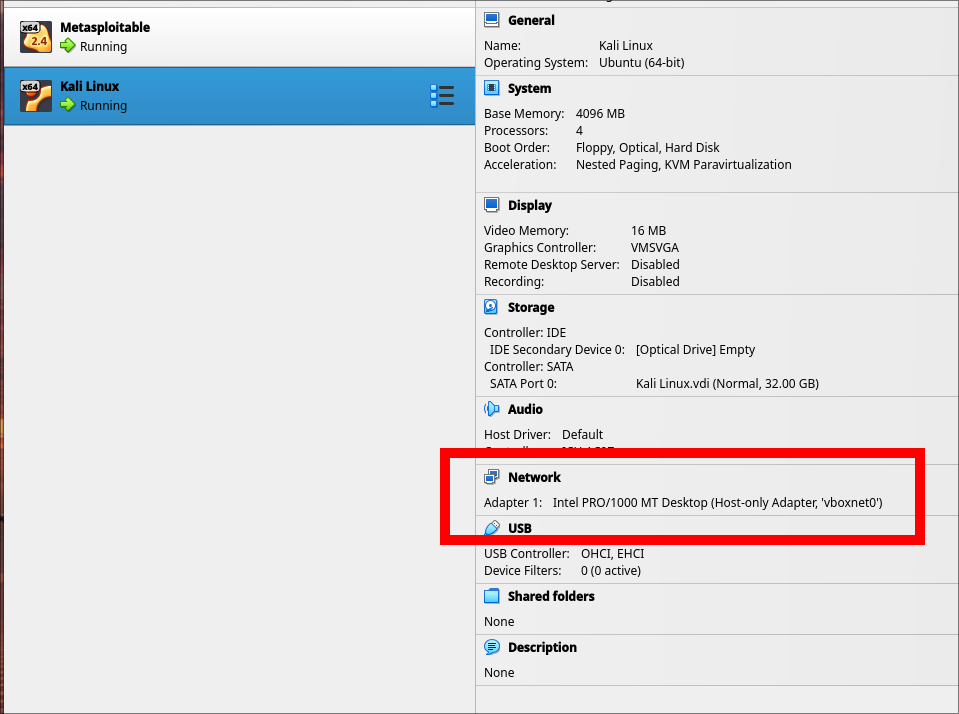
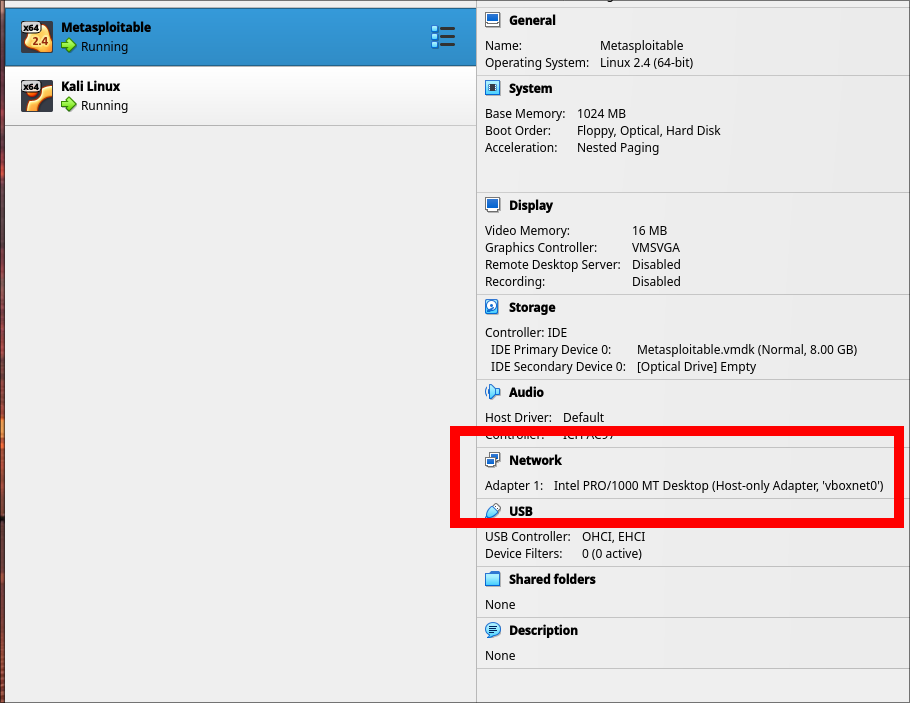 2. Verify the network connectivity by pinging Metasploitable from Kali Linux
2. Verify the network connectivity by pinging Metasploitable from Kali Linux
Task 2 - Nmap Scan for Open Ports and Vulnerabilities
Use nmap to perform a vulnerability scan of the metasploitable machine.
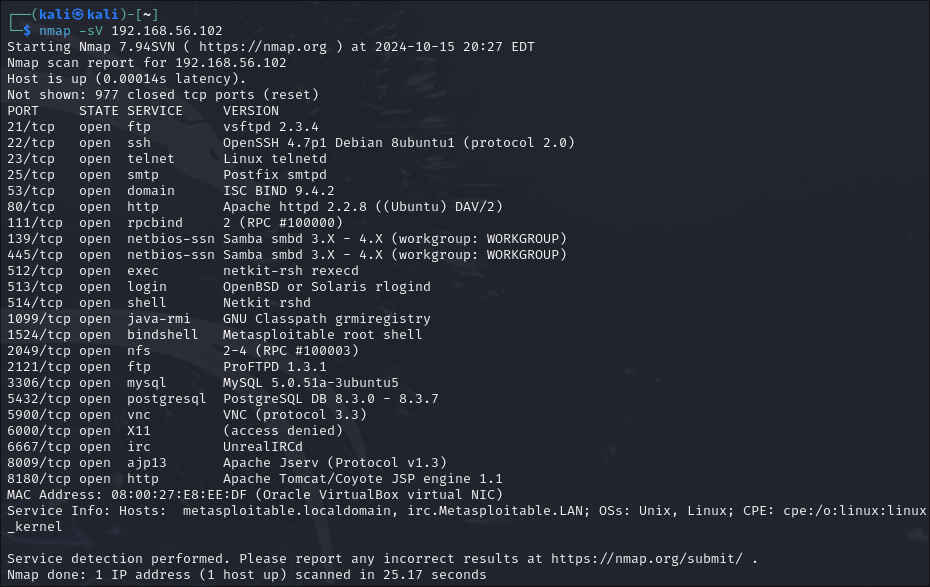
Task 3 - Installing and Launching Armitage
Install Armitage and set it up to connect with the Metasploit framework.
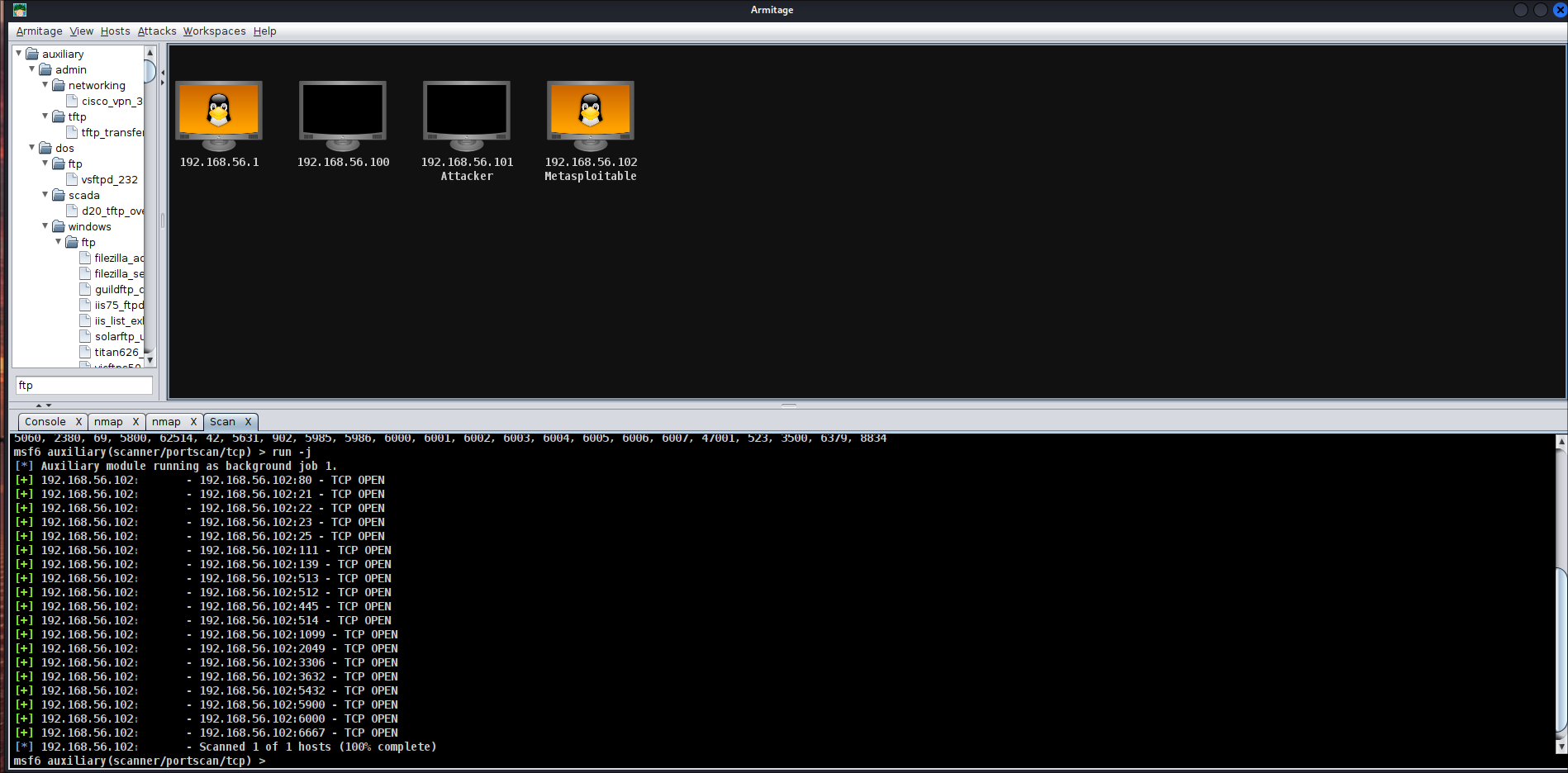
Task 4 - Perform a Vulnerability Scan with Armitage
Use Armitage to scan the Metasploitable machine and identify potential vulnerabilities.
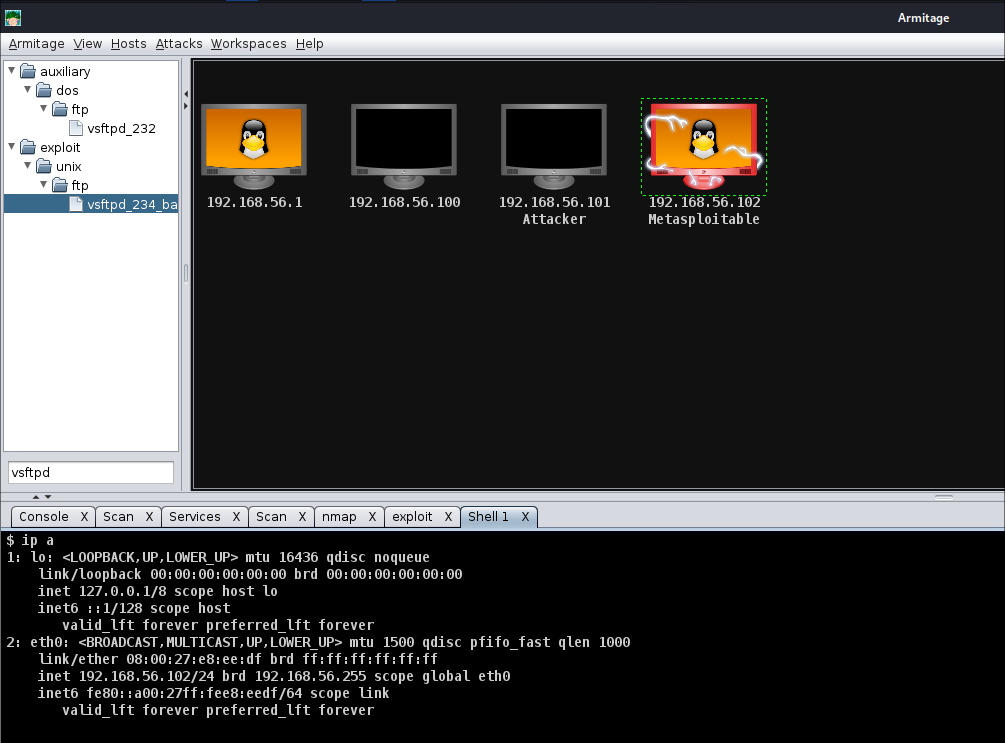
Task 5 - Exploiting a Vulnerability Using Armitage
Use Armitage to exploit a vulnerability on the Metasploitable machine and gain access.
Reflection
The nmap tool is suprisingly easy, yet very powerful. After using it on this assignment, I used it to learn about vulnerabilities on my home server. I found that I had ports 80, 443, and 22 open. I did not realize that I had left it open, and I couldn't remembery why I had it open in the first place. I then used a remote network configuration tool to close port 80. After running nmap again, I saw that I had successfully closed the port.
I really enjoyed using Armitage as an easy introduction to the Metasploit Framework. At this point, I really only plan to use it as a learning tool to get used to deploying attacks and scanning networks. Today, for example, I learned about scanning IP ranges. My next step is to switch to the metasploit CLI.