3.1 KiB
Ethical Hacking in ECE Assignment 2 - Aidan Sharpe
Assignment Tasks
Task 1
Create a directory named ethics_lab and manage files within it using commands like mkdir, cd, mv, and touch.
 Create a directory called
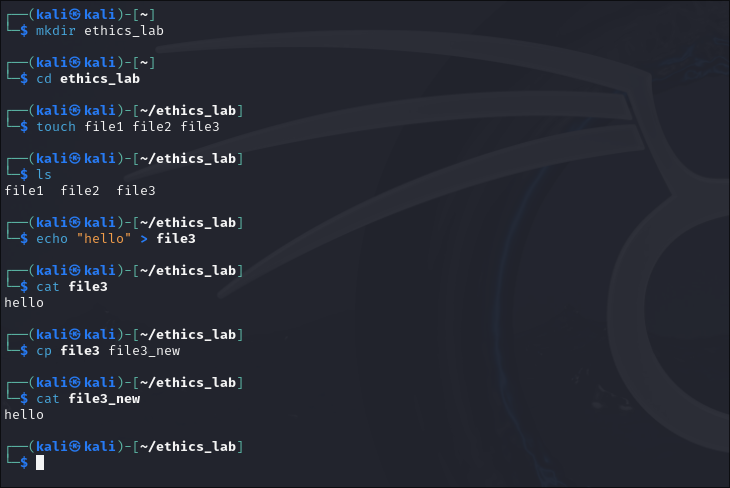
Create a directory called ethics_lab using the mkdir command. Then navigate to ethics_lab using cd. Create three files (file1, file2, and file3) using the touch command. Show the contents of the ethics_lab directory using ls. Write the text "hello" into file3 using echo and the write to file symbol (>). Print the contents of file3 to the terminal using the cat command.
Task 2
Monitor and manage processes on your system using tools like ps, top, and kill. Identify and terminate a process.
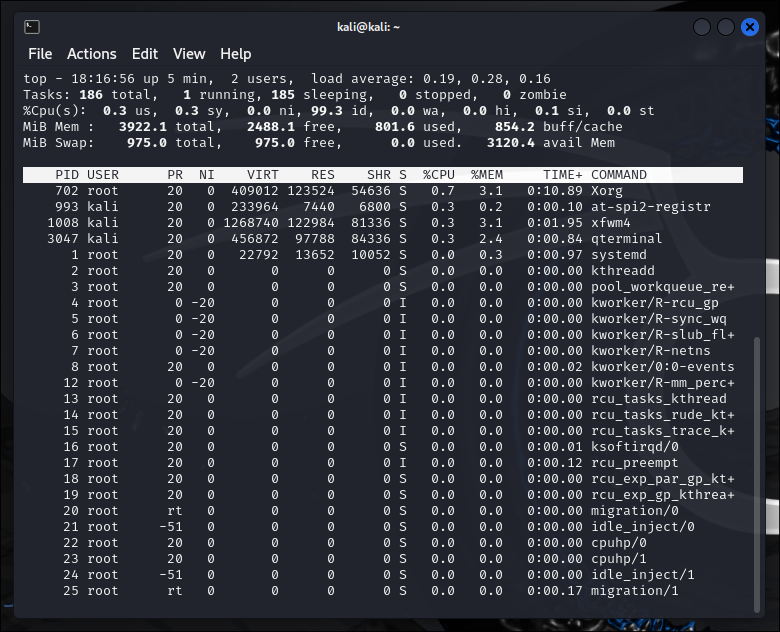
View an active, sorted list of all tasks running on the system using top.
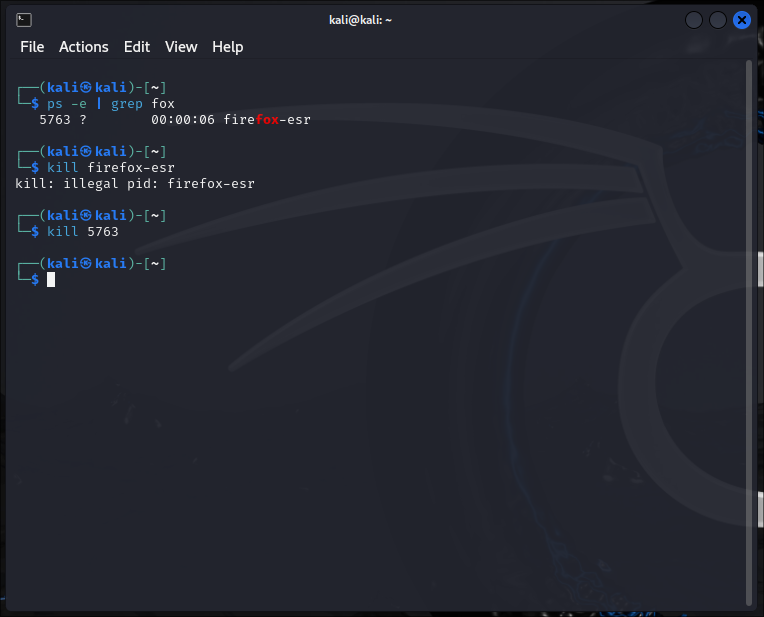
List all tasks running on the system using ps -e then pass the output into grep and filter for the text "fox". This shows the information for the firefox-esr task. The number at the beginning of the line is the process identifier, and the process can be ended by executing kill followed by that process ID.
Task 3
Use ifconfig/ip a, ping, and netstat.
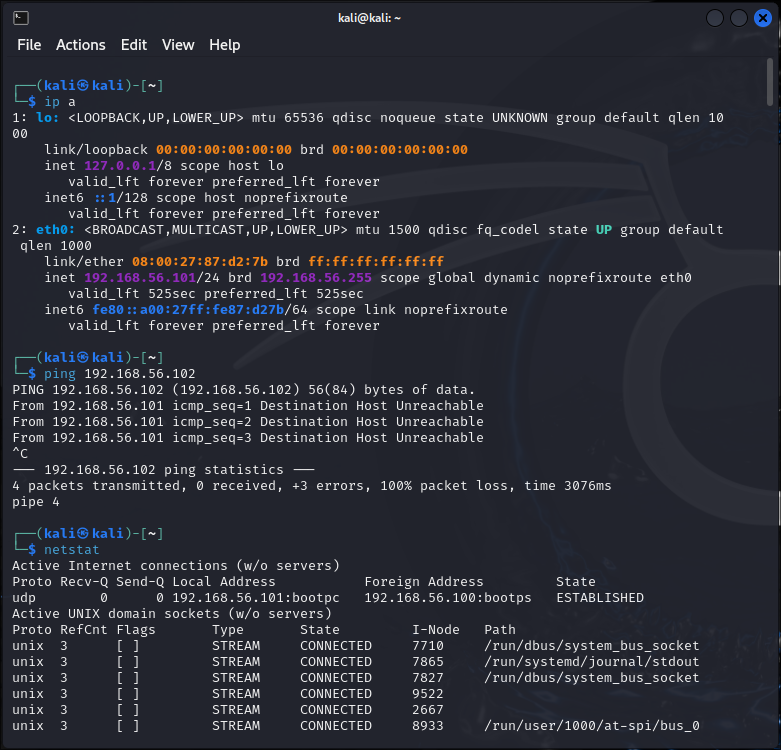
Running ip a shows IP address information. For example, we can see that the current IP address is 192.168.56.101. We also ran this command on another virtual machine and found that its IP address was 192.168.56.102, so we can ping it using ping to see if a connection can be established. Runningnetstat shows a list of network connections.
Task 4
Set up a second VM and connect to it using ssh.
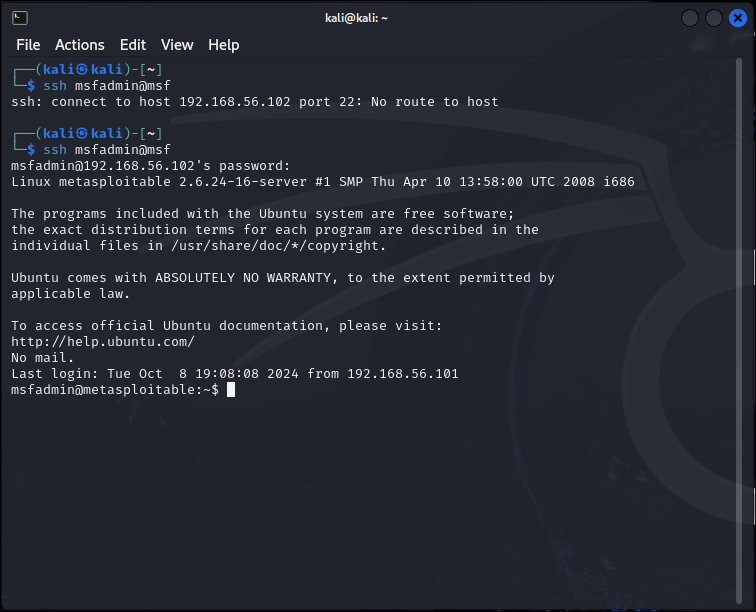
Prior to running the command, a host configuration was created called msf. This contained the known ip address and the preferred key algorithm. The command ssh msfadmin@msf creates a login tunnel for the user account msfadmin between the host and remote system.
Task 5
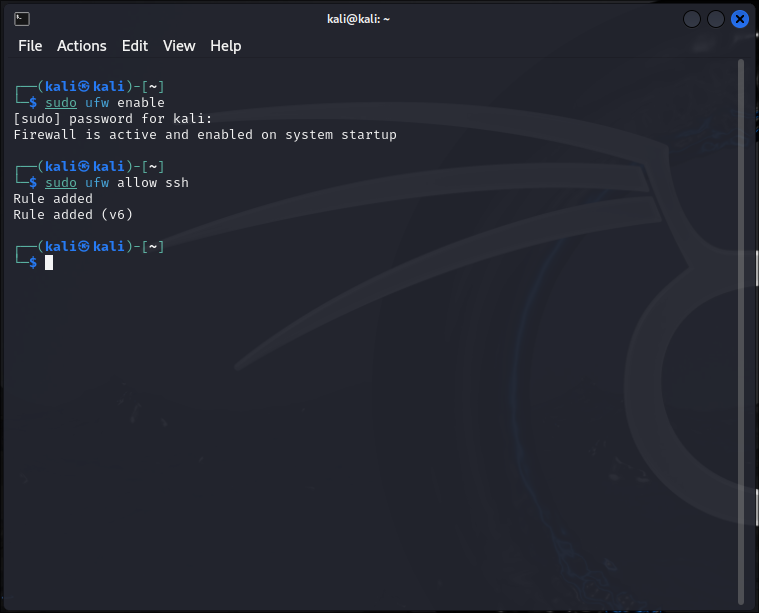
Configure the firewall using ufw. Enable the firewall and allow SSH traffic.
Reflection
Learning basic Linux command is an important skill for ethical hacking for multiple reasons.
Reason 1 - Most Ethical Hacking Tools Run on Linux
Most ethical hacking tools run on or are designed specifically for Linux machines. Knowing how to better use the machines that your tools are running on is always advantageous.
Reason 2 - Most Servers Run Linux
Since over 90% of the servers on the internet run Linux, that means that most databases (the places where pretty much all valuable information is stored) are hosted on Linux-based servers. By being familiar with basic Linux commands, navigating remote server file systems becomes a much easier task.
Skills Gained from This Assignment
One skill I learned from this assignment is forcing a specific key algorithm for different hosts. While I have used SSH many times in the past, I was not aware that different machines restricted the type of keys used. Frankly, I thought they all used the same type of key. After completing this exercises, I am now practiced in the configuration of host key algorithms.